How to avoid the traps!
With the increase of teleworking, the risk of being cyber-attacked is high.
A lot of Small and Medium Businesses had to develop solutions to let people telework at the beginning of the pandemy. Lot of them were not prepared to it and made choices that may have impact on the security of their systems.
People are less and less interacting each other with the distance. There are more online and email conversations that will increase the risk too. Being hacked can have big consequences to your data and may interrupt your activities for a while.
There are multiple threats and faults can come from softwares or humans. That is why we want to explain you, what are the different kind of threats to auto-evaluate your vulnerability.
The different risks
Phishing
The phishing is a practice in which the hacker try to usurp an identity of someone in the company or any other people that may have some authority. This way, he will try to ask for some secret information (passwords) or any urgent payment for a supplier, taxes, etc. It is part of the social hacking which requires no particular skill in computing or development and work on persuasion.
How does it look like?
Through emails: the email is one of the best canal, it looks like it has been sent from one of your colleague or any institution (bank, energy company, web provider, web platforms, etc.) but in reality it comes from another account ready to get a quick response.
It usually explains you that you have some issues with your account or have to proceed to a password renewal or do a quick payment to avoid penalties. In reality It will try to scary you so you will click on the link attached or answer by email to the sender directly.
Ouvrir un courriel est rarement dangereux. Ce sont les liens web et les pièces jointes attachées qui le sont. Aussi dans le cadre du hameçonnage, les courriels vous invite sous un certain prétexte à venir mettre à jour des informations confidentielles (carte bancaire, mots de passe, etc.) en vous proposant un lien directement dans le courriel pour venir vous authentifier.
This link or the sender is a fake. Sometimes it will looks like the real website of the company/institution but in reality it is just a copy. Their only purpose is to make you login or complete a payment or a form with secret information like credentials. This way they can take controle of an account or credit card information.
This method can be also used by phone, online discussions, etc.
How to avoid it
You can use these 2 rules :
You have to make your colleagues and employees aware of the risk. Specially person that are not used to using a computer or internet. They should never answer to any unusual situation or exceptional situations by email. Like an email from the boss asking to pay a supplier quickly for example.
If they have a doubt, they should identify the sender. If they know the person, always try to make a call or contact directly the company or the institution for confirmations.
If there is any link and you have a doubt, always connect to the official website by a web browser instead of clicking on the link sent by email.
There are some things to know if you want to verify if the email is a phishing but ther are not always visibile :
- - First tip : The wording or the grammar is not good. It usually comes from hackers living in another country.
- The graphic design can look a bit different from original logo, original email template or real website.
- One last tip is the domain used in the sender email or in any url link. Sometimes you can identify a phishing attempt because the sender email address is not the real one or the link redirect you to a website with a different URL than the real one. Example : you have to pay a UPS invoice but the email redirect you to a website with the URL www.ups-forms1.com. This is a fake one because the domain of UPS website is : www.ups.com and not www.ups-forms1.com.
Be careful, malicious attacks can be more subtile. It is just some clues that will help you to detect threats.
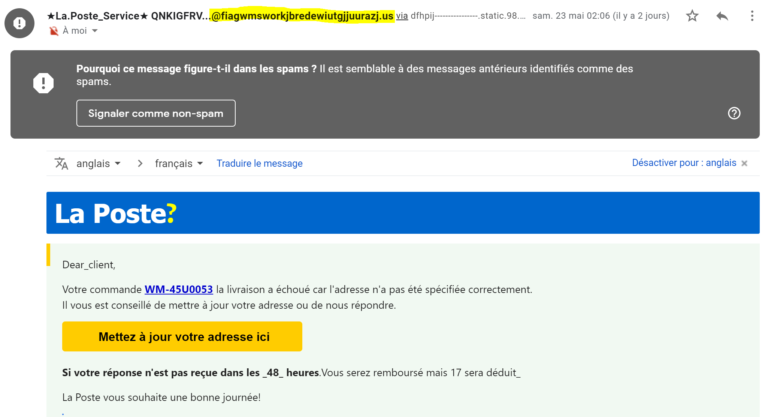
Here above, some example including different points :
- The email is asking for confidential data.
- The email is mispelled and the logo/company name do not fit with the original design.
- Web domain of the sender is not the real one.
The Ransonware
Ransonware is an encryption tool. It alters documents and makes them unreadable without the decryption key.
Imagine having database locked or different folders of file. It can have significant impact on your business and without a backup, you can lose everything.
The ransonware can be triggered manually if someone get into your system but it can also be executed from another software like a malicious email attachment.
It will instantly encrypt most of your programs in your system or your network.
They usually send you an email and ask for money in order to restaure your documents.
Virus, Trojan and other malwares
Those threats are usually managed by most of the antivirus softwares but they can also gather information or tracking your activities in order to get crucial information (password, etc.).
Good practices
1. Sensibilize your team about the risk of social hacking and phishing.
As we explained previously, it is very important to understand how people can get critic information just with social hacking and phishing. People should always be aware and able to detect uncommon or suspicious email before opening it.
2. Save your data!
Dans un monde 100% informatisé les données ont trop de valeur pour qu’elles soient négligées. La perte de ces données seraient pourrait jusqu’à mettre en péril votre entreprise.
You must set up a data recovery plan. Here some advices :
- One save is not enough, store multiple saves on different disks, storage options.
- Have one save located in another place in case of massive hack or any incident (fire, flood, etc.).
- Monitor your saves and make sure the service is always running. Test it regularly.
3. Make sure your network and your equipments are secure
- Firewall;
- Antispam;
- Anti-virus;
- Up-to-date operating system
Autant d’outils clé pour protéger les ordinateurs personnels.
4. Securize your server access and your passwords.
5. Make sure your passwords didn't leak.
A lot of users use their professionnal accounts in web sites.
When those websites are attacked, some confidential data are leaked, including the passwords and the email addresses.
If people usually use the same password, it can help the hackers to get into your system or hack the email.
Some websites exist to verify if your email and password combination has been leaked like www.haveibeenpwned.com. www.haveibeenpwned.com
6. Never open suspicious attachment or link in your emails.
A little reminder of what a suspicious email is :
- Anything asking your to change confidential data or make a payment in urgent situation.
- Sender email address has a weird webdomain (information after the @ symbol). ex : you get an email from Bell but the sender is : george@bell-canada-provider.com (Which is not the exact webdomain of bell.ca)
- The design and logo don't look like the original design of the company.
7. Test your staff and your systems.
Des compagnies proposent des services afin de réaliser un stress-test de votre infrastructure, s’assurer que votre personnel est éduqué et vigilant aux pièges et la protection des données sensibles.
Ces derniers simuleront des attaques dans votre quotidien sur une période donnée et vous fourniront des pistes d’amélioration pour sécuriser votre système ou sensibiliser vos collaborateurs.

